Data Erasure
Degaussing Services

Vector Data Recovery provides a high-quality degaussing service based on ISO 9001:2015 Certified – Secure Electronic Data Erasure & Destruction Services. We provide a quality-checking process to demagnetize the disk so that all data stored on the disk is permanently destroyed. Thus making the disk impossible to be recovered with any recovery tools available.
Secure Erase HDD

Vector Data Recovery provides ISO 9001 Certified for high-quality Secure Electronic Data Erasure Services on any storage media such as PATA, SATA, SCSI, or SAS. There are many options for erasure. One of them is Software Erase, by overwriting the sector of the disk with a new value with a certain amount of passes to ensure that the data is harder to recover. But we also provide a better option than software erase, 「Secure Erase」 which initiates the drive’s internal secure erase command, and security erase unit.
Secure Data Destruction

One of the key solutions to eliminate the risk of data falling into the wrong hands is to degauss hard drives prior to disposal. Hard drive degaussers use powerful magnets or an electromechanical 「pulse」 to erase data from hard drives. Similarly, tapes should also be properly degaussed before disposal.
In fact, Requirements for hard drives to be degaussed in a PCI DSS/NIST SP 800-36/NIST SP 800-88/HIPAA/PIPEDA/HMG CESG IS5 Degausser and then physically destroyed prior to disposal.
Degausser operates in accordance with the ISO27001 standard. ProDevice ASM120 is a perfect solution for companies and institutions that care for the highest standards related to the protection of confidential data, defined by GDPR.
IT Asset Disposition – ITAD
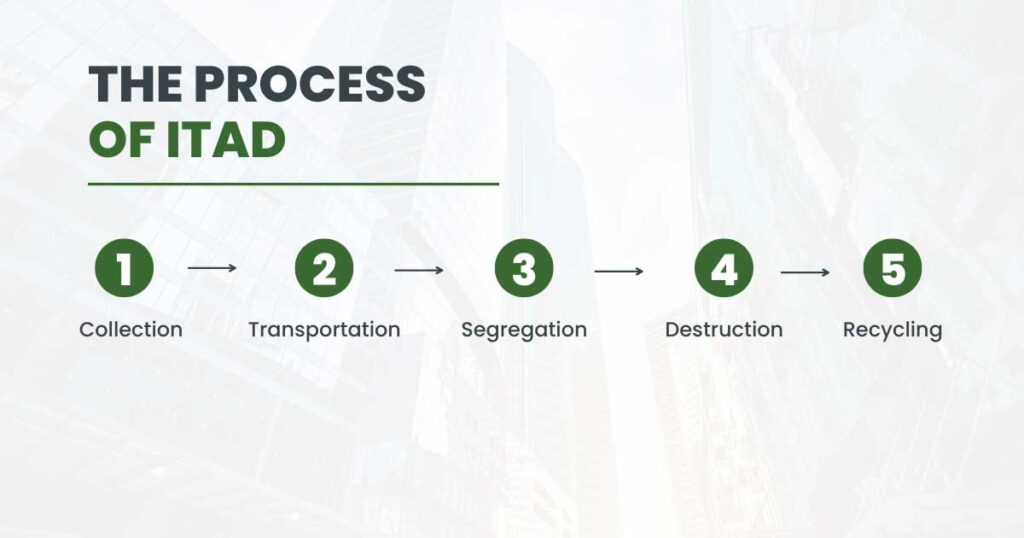
Proper IT asset disposal is becoming more and more important not just on environmental issues but also on data confidentiality.
Many organizations do not have the dedicated resources or the bulk quantity to justify the investment in procuring the equipment. They may choose to outsource such destruction and disposal. Outsourcing can be affordable and safe when done properly. If you choose this option, ask what methods will be used, where your items will be kept prior to destruction, or if there are any on-site services, what happens to destroyed waste, and what proof you will get that those items were actually destroyed.
Data security is an ongoing process, by being aware of the threats and understanding the destruction options, you will be in a much better position to protect your business and yourself. You will have complete peace of mind that you have left nothing behind.
Data Terminator provides complete IT asset disposal solutions. Our capabilities include the management of the complete disposal process of asset verification, secure data sanitization and asset de-classification, and proper destruction, and disposal.